Information Security Laboratory. Keylogger - keylogger What types of spyware are there and where to download them
Various spy programs are necessary in conditions where many people have access to one computer.
In these circumstances, the user may want to know which sites were visited from his computer (for example, by children), whether credit cards were stolen using saved passwords, etc. To clarify these issues, it will be necessary.
Our review will allow you to make the best choice.
Features of choice
What exactly is a keylogger? This is a program that, strictly speaking, is not directly related to the keyboard.
It is installed in the computer's memory and acts on. Often, signs of its activity are not visible on the computer unless you specifically look for them.
Such a program interacts indirectly with the keyboard, that is, it works with a program on the PC that converts the signals received by the processor as a result of pressing buttons into text when printing.
That is, the action of such software is aimed at collecting information entered through the keyboard.
Such utilities come in different types - with some you can view all the text typed on the keyboard, with others - only what was typed in the browser or in any selected application.
Some programs provide the ability to configure such indicators, others do not.
They also differ from each other in the degree of secrecy. For example, the activity of some is obvious, a shortcut remains on the Desktop, etc., such programs are suitable for monitoring the activities of, for example, children.
Traces of the presence and activity of others are not noticeable at all - they act hidden and are suitable for installation on someone else’s computer, when the fact of installation needs to be hidden from a third-party user.
Given such diversity, choosing the most suitable software can be quite difficult.
This material presents the TOP of the best programs that can be used for this purpose. It is easier to choose the right one among them.
Specifications
To simplify the software selection process, the table below shows the main comparative characteristics of all programs included in the TOP.
| Name | License type | Type of information collected | Functional | Design |
|---|---|---|---|---|
| SC-KeyLog | For free | All | Wide | Simplified |
| WideStep Handy Keylogger | Free/Paid | All | Wide | Improved |
| Actual Spy | Paid | All | Very wide | Standard |
| EliteKeylogger | Paid | All | Wide | Standard |
| The Rat! | Free/Paid | Less than previous | Quite wide | Unaesthetic |
| SPYGO | For free | Depending on version | Depending on version | Standard Windows appearance |
| Ardamax Keylogger 2.9 | For free | From the keyboard | Narrowed | Simplified |
| NS Keylogger Personal Monitor 3.8 | For free | All | Narrowed | Simplified |
| KGB Spy | Paid | From the keyboard + open programs | Narrow | Simple |
| Golden Keylogger 1.32 | For free | From the keyboard | Very narrow | Simple |
Based on the characteristics from this table, it is easy to choose the program that best suits your specific requirements.
These utilities are described in more detail below.
SC-KeyLog
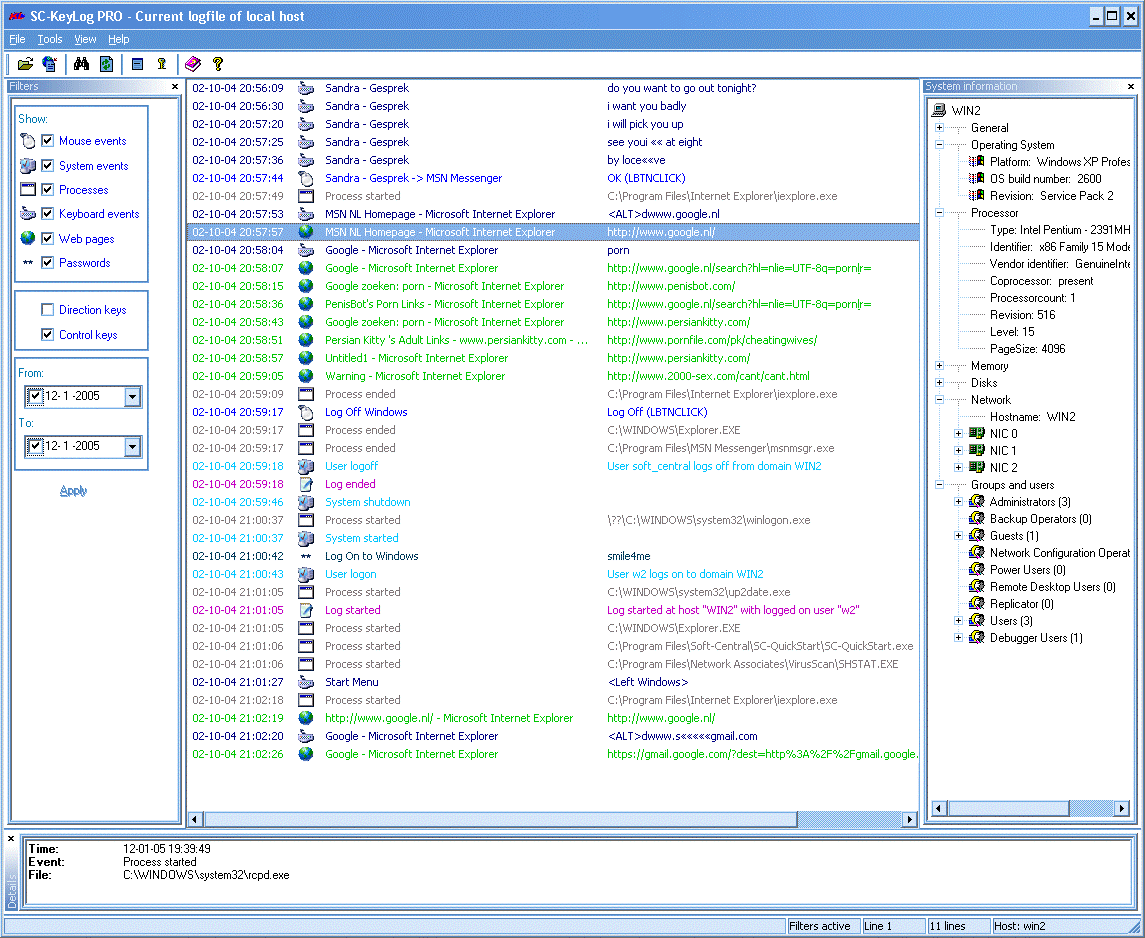
This is a voluminous and functional spy program that is distributed free of charge.
In addition to specifically tracking information entered from the keyboard, it is also able to collect addresses of visited sites, passwords, and open browser windows.
Provides complete information about all actions performed on the computer. In this case, the generated file can be viewed remotely from another device.
- Possibility of remote access to a file from another device;
- No traces of program activity on the computer with the correct settings;
- Variety of collected data - information about almost all actions on the PC can be accessed.
- Saves passwords only up to NT0;
- Too simple menu and unaesthetic design;
- A rather inconvenient format for displaying the result.
What do users who actively use this software say? “Absolutely invisible to the user”, “Data arrives regularly by email.”
WideStep Handy Keylogger

This application is distributed free of charge. The full paid version costs $35.
Quite an interesting and functional program that is worth the money if you are willing to pay it.
Distinctive feature– the ability to send recorded data at a specified frequency. Otherwise it works fine, often more stable than other programs on this list.
- Collection of various types of information;
- Complete invisibility of work on the user’s computer;
- Simple interface and controls.
- The design is better than the previous program, but still not great;
- The result display format is inconvenient;
- The paid version is quite expensive.
Users' opinions about this software are as follows: “Convenient, simple and functional program. Quite invisible when working."
Actual Spy

This is a functional and complex paid program that costs 600 rubles. However, it has a demo version that is free.
Feature of this software– ability in a given period of time.
This helps solve the problem of entering a graphic password/key, which has recently become widespread.
- Many types of information collected plus the ability to take screenshots from the screen during a specified period;
- A large number of other additional functions and features;
- Records not only actions, but also the time they were performed;
- Encrypts the generated log.
- The duration of work (collection of information) in the free demo version is 40 minutes;
- Paid distribution, although a more or less reasonable price;
- The weight of the program is quite large.
User reviews of this application are as follows: “The program is excellent. Well done programmers!”
EliteKeylogger

Paid program with a fairly high price– 69 dollars. It operates completely undetectably on a PC in low-level mode, making it almost completely undetectable.
Interesting and convenient feature– automatic launch of software, occurring simultaneously with the launch of the system itself.
It is difficult to detect or not detected at all even by special anti-keyloggers.
- Completely hidden action and difficult to detect;
- Low-level driver-type operating format and automatic startup when the system boots;
- It also tracks the presses of not only the main, but also the service keys on the keyboard.
- A rather complex system for installing the program on a PC;
- The program is expensive, but you can find an old hacked version on the Russian Internet;
- A rather complex system of individual program settings, which, however, justifies itself.
What do users say about this software? “Good program”, “A little short of Jetlogger.”
The Rat!

Quite a common and popular, functional utility with a paid license.
However, for private use, a free demo version is provided for a limited period.
The program is very simple– any advanced user can write the same. However, it is completely undetectable by antiviruses and special programs that detect such software.
- Simplicity, functionality and high stability;
- Minimum file weight and space occupied by it on the computer;
- Quite a lot of settings.
- A rather unpleasant design, made in black, white and red;
- The functionality is somewhat narrower than in the programs described before;
- Inconvenient viewing of the log and generally inconvenient interface and use.
Users say the following about this program: “It works stably, but is a bit simple,” “The program is good, it allows you to collect data unnoticed.”
SPYGO

This is a fundamentally new keylogger, designed to work on and developed by a Russian programmer.
How can you find out what your child or employee is doing on the computer? What sites does he visit, with whom does he communicate, what and to whom does he write?
For this purpose, there are spy programs - a special type of software that, unnoticed by the user, collects information about all his actions. Computer spy software will solve this problem.

Spyware for a computer should not be confused with a Trojan: the first is absolutely legitimate and is installed with the knowledge of the administrator, the second gets onto the PC illegally and carries out hidden malicious activities.
However, hackers can also use legitimate tracking programs.
Spyware applications are most often installed by business managers and system administrators to monitor employees, parents to spy on children, jealous spouses, etc. At the same time, the “victim” may know that she is being monitored, but most often she does not know.
Review and comparison of five popular spyware programs
NeoSpy
NeoSpy is a universal keyboard, screen and user activity spy program. NeoSpy works invisibly and can hide its presence even during installation.
The user who installs the program has the opportunity to choose one of two installation modes - administrator and hidden. In the first mode, the program is installed openly - it creates a shortcut on the desktop and a folder in the Program Files directory, in the second - hidden.
Program processes do not appear in Windows Task Manager or third-party task managers.
The functionality of NeoSpy is quite wide and the program can be used both as home monitoring and in offices to monitor employees.
The spy program is distributed in three versions under a shareware license. The price is 820-1990 rubles, but it can also work for free (even in hidden mode) with restrictions when viewing reports.
What NeoSpy can do:
- monitor the keyboard;
- monitor website visits;
- show the user’s screen in real time via the Internet from another computer or tablet;
- take screenshots and save images from your webcam;
- monitor system events (turning on, shutting down, computer downtime, connecting removable media);
- intercept the contents of the clipboard;
- Monitor the use of Internet instant messengers, record Skype calls;
- intercept data sent for printing and copied to external media;
- keep statistics of computer work;
- send laptop coordinates (calculated over Wi-Fi).
Thanks to the Russian-language interface, a wide range of functions, correct keyboard interception and a completely hidden operating mode in the system, NeoSpy receives the maximum rating when choosing programs for user control.
Real Spy Monitor
The next spy is Real Spy Monitor. This English-language program not only has tracking functions, but can also block certain actions on the computer. Therefore, it is often used as a parental control tool.
For each account in the Real Spy Monitor settings, you can create your own ban policy, for example, for visiting certain sites.
Unfortunately, due to the lack of an English-language interface, it is more difficult to understand the operation of Real Spy Monitor, despite the graphical thumbnails for the buttons.
The program is also paid. The license costs from $39.95.
Real Spy Monitor features:
- interception of keystrokes, clipboard contents, system events, websites, instant messengers, mail;
- work in semi-hidden mode (without an active window, but with the process displayed in the task manager);
- working with multiple accounts;
- selective autostart for different accounts.
In general, many users like Real Spy Monitor; the disadvantages include the high cost, lack of a Russian-language interface, and display of the process in the task manager.
Actual Spy
The developers position Actual Spy as a keylogger (keylogger), although the program can do more than just record keystrokes.
It monitors the contents of the clipboard, takes screenshots, monitors site visits, and other things that are included in the main set of spies we examined.
When installed, Actual Spy creates a shortcut in the Start menu so it can be noticed by the user. The launch also occurs openly - to hide the program window you need to press certain keys.
Actual Spy's capabilities are not much different from those of its competitors. Among the shortcomings, users noted that it correctly records keystrokes only in the English layout.
SpyGo
SpyGo - spy kit for home use. Can also be used in offices to monitor employees.
To start monitoring, just click the “Start” button in SpyGo.
SpyGo is distributed under a shareware license and costs 990-2990 rubles depending on the set of functions.
In trial versions, monitoring duration is limited to 20 minutes per day, and sending reports to email and FTP is also not available.
Main features of SpyGo:
- keystroke monitoring;
- recording all actions on the computer (launching programs, operations with files, etc.);
- control of visits to web resources (history, search queries, frequently visited sites, duration of stay on the site);
- recording what is happening on the screen;
- saving the contents of the clipboard;
- listening to the environment (if there is a microphone);
- monitoring of system events (times of turning on and off the computer, downtime, connecting flash drives, disks, etc.).
Important! The disadvantages of SpyGo, according to users, include the fact that it does not support all versions of Windows, when sending reports it often throws errors and is quite easily unmasked.
Snitch
Snitch - the name of this program translates as “snitch”, and is very unfriendly towards the user. Snitch spies on computer activities. It works hidden, does not require complex settings and has little effect on system performance.
The program is released in a single version.
Features and Features of Snitch:
- monitoring of the keyboard, clipboard, system events, web surfing and communication in instant messengers;
- compilation of summary reports and graphs of monitored events;
- undemanding network configuration;
- protection against unauthorized termination of the program process;
- surveillance is carried out even in the absence of access to the network.
Among the shortcomings, you can notice conflicts with antiviruses
How to detect a spy on your computer?
Finding spyware on a computer that doesn’t show itself outwardly is difficult, but not impossible.
So, despite their legitimacy, the applications we reviewed can be recognized by special antiviruses,“tailored” for searching for spyware (Trojans with spying functions), so we recommend adding the installed program to the exclusion list of such antiviruses.
And if you do not need to remove the spy, but only need to disguise your actions from it, you can use anti-spying tools that, despite actively spying on you, will prevent the interception of keyboard events and screenshots.
Then your correspondence and passwords will not fall into the wrong hands.
The hacker world can be divided into three groups of attackers:
1) “Skids” (script kiddies) – little novice hackers who collect well-known pieces of code and utilities and use them to create some simple malware.
2) “Buyers” are unscrupulous entrepreneurs, teenagers and other thrill-seekers. They buy services for writing such software on the Internet, collect various private information with its help, and possibly resell it.
3) “Black Hat Coders” - programming gurus and architecture experts. They write code in a notepad and develop new exploits from scratch.
Can someone with good programming skills become the last one? I don't think you'll start creating something like regin (link) after attending a few DEFCON sessions. On the other hand, I believe that an information security officer should master some of the concepts on which malware is built.
Why do information security personnel need these dubious skills?
Know your enemy. As we discussed on the Inside Out blog, you need to think like the offender to stop him. I am an information security specialist at Varonis and in my experience, you will be stronger in this craft if you understand what moves an attacker will make. So I decided to start a series of posts about the details that go behind malware and the different families of hacking tools. Once you realize how easy it is to create undetectable software, you may want to reconsider your enterprise's security policies. Now in more detail.
For this informal "hacking 101" class, you need some programming knowledge (C# and java) and a basic understanding of Windows architecture. Keep in mind that in reality the malware is written in C/C++/Delphi so as not to depend on frameworks.
Keylogger
A keylogger is software or some kind of physical device that can intercept and remember keystrokes on a compromised machine. This can be thought of as a digital trap for every keystroke on a keyboard.
Often this function is implemented in other, more complex software, for example, Trojans (Remote Access Trojans RATS), which ensure the delivery of intercepted data back to the attacker. There are also hardware keyloggers, but they are less common because... require direct physical access to the machine.
However, creating basic keylogger functions is fairly easy to program. WARNING. If you want to try any of the following, make sure you have the permissions and are not disrupting the existing environment, and it's best to do it all on an isolated VM. Next, this code will not be optimized, I will just show you lines of code that can accomplish the task, this is not the most elegant or optimal way. And finally, I will not tell you how to make a keylogger resistant to reboots or try to make it completely undetectable using special programming techniques, as well as protection from deletion even if it is detected.
To connect to the keyboard you just need to use 2 lines in C#:
1. 2. 3. public static extern int GetAsyncKeyState(Int32 i);
You can learn more about the GetAsyncKeyState function on MSDN:
To understand: this function determines whether a key was pressed or released at the time of the call and whether it was pressed after the previous call. Now we constantly call this function to receive data from the keyboard:
1. while (true) 2. ( 3. Thread.Sleep(100); 4. for (Int32 i = 0; i< 255; i++) 5. { 6. int state = GetAsyncKeyState(i); 7. if (state == 1 || state == -32767) 8. { 9. Console.WriteLine((Keys)i); 10. 11. } 12. } 13. }
What's going on here? This loop will poll each key every 100ms to determine its state. If one of them is pressed (or has been pressed), a message about this will be displayed on the console. In real life, this data is buffered and sent to the attacker.
Smart keylogger
Wait, is there any point in trying to remove all the information from all applications?
The code above pulls raw keyboard input from whatever window and input field currently has focus. If your goal is credit card numbers and passwords, then this approach is not very effective. For real-world scenarios, when such keyloggers are executed on hundreds or thousands of machines, subsequent data parsing can become very long and ultimately meaningless, because Information valuable to an attacker may be out of date by then.
Let's assume that I want to obtain Facebook or Gmail credentials to sell likes. Then a new idea is to activate keylogging only when the browser window is active and the word Gmail or facebook is in the page title. By using this method I increase the chances of obtaining credentials.
Second version of the code:
1. while (true) 2. ( 3. IntPtr handle = GetForegroundWindow(); 4. if (GetWindowText(handle, buff, chars) > 0) 5. ( 6. string line = buff.ToString(); 7. if (line.Contains("Gmail")|| line.Contains("Facebook - Log In or Sign Up")) 8. ( 9. //keyboard check 10. ) 11. ) 12. Thread.Sleep(100); 13. )
This snippet will detect the active window every 100ms. This is done using the GetForegroundWindow function (more information on MSDN). The page title is stored in the buff variable, if it contains gmail or facebook, then the keyboard scanning fragment is called.
By doing this, we ensured that the keyboard is scanned only when the browser window is open on the facebook and gmail sites.
An even smarter keylogger
Let's assume that the attacker was able to obtain the data using a code similar to ours. Let’s also assume that he is ambitious enough to infect tens or hundreds of thousands of machines. Result: a huge file with gigabytes of text in which the necessary information still needs to be found. It's time to get acquainted with regular expressions or regex. This is something like a mini language for creating certain templates and scanning text for compliance with given templates. You can find out more here.
To simplify, I will immediately give ready-made expressions that correspond to login names and passwords:
1. //Looking for postal address 2. ^[\w!#$%&"*+\-/=?\^_`(|)~]+(\.[\w!#$%&"*+ \-/=?\^_`(|)~]+)*@((([\-\w]+\.)+(2,4))|(((1,3)\.)( 3)(1,3)))$ 3. 4. 5. //Looking for password 6. (?=^.(6,)$)(?=.*\d)(?=.*)
These expressions are here as a hint to what can be done using them. Using regular expressions, you can search (and find!) any constructs that have a specific and unchanging format, for example, passport numbers, credit cards, accounts, and even passwords.
Indeed, regular expressions are not the most readable type of code, but they are one of the programmer's best friends if there are text parsing tasks. Java, C#, JavaScript and other popular languages already have ready-made functions into which you can pass regular regular expressions.
For C# it looks like this:
1. Regex re = new Regex(@"^[\w!#$%&"*+\-/=?\^_`(|)~]+(\.[\w!#$%&"* +\-/=?\^_`(|)~]+)*@((([\-\w]+\.)+(2,4))|(((1,3)\.) (3)(1,3)))$"); 2. Regex re2 = new Regex(@"(?=^.(6,)$)(?=.*\d)(?=.*)"); 3. string email = " [email protected]"; 4. string pass = "abcde3FG"; 5. Match result = re.Match(email); 6. Match result2 = re2.Match(pass);
Where the first expression (re) will match any email, and the second (re2) will match any alphanumeric structure greater than 6 characters.
Free and completely undetectable
In my example, I used Visual Studio - you can use your favorite environment - to create such a keylogger in 30 minutes.
If I were a real attacker, then I would aim at some real target (banking sites, social networks, etc.) and modify the code to match these goals. Of course, I would also run a phishing email campaign with our program, masquerading as a regular invoice or other attachment.
One question remains: will such software really be undetectable by security programs?
I compiled my code and checked the exe file on the Virustotal website. This is a web-based tool that calculates the hash of the file you downloaded and searches it against a database of known viruses. Surprise! Naturally nothing was found.

This is the main point! You can always change the code and develop, always being a few steps ahead of the threat scanners. If you are able to write your own code it is almost guaranteed to be undetectable. You can read the full analysis on this page.
The main purpose of this article is to show that using antiviruses alone you will not be able to fully ensure security in your enterprise. A more in-depth assessment of the actions of all users and even services is needed to identify potentially malicious actions.
In the next article I will show how to make a truly undetectable version of such software.
Personal Monitor
YOUR CHOICE
for parental control
The program is very easy to use and also allows you to fully control what your child is doing on the Internet.
These are the reviews users leave about the Mipko Personal Monitor keylogger. The first version of the program was released more than 10 years ago, and the number of its installations has exceeded 2,500,000. This is the best keylogger, which also has a free trial period!
Protection for your child
personal monitor for windows
Free version
for 3 days
Keylogger Mipko Personal Monitor today:
Video review of the Mipko Personal Monitor program from Alexander Medvedev
Free trial period
If you download the Mipko Personal Monitor keylogger right now, you will be able to use free 3-day trial period without functionality limitations.
Well, if within 7 days after purchasing the program you are disappointed with it, then we will refund your money without any questions asked.
What the Mipko Personal Monitor keylogger can do
The program intercepts and remembers absolutely all keystrokes. And it doesn’t matter where the user works - in any program, browser, games, chats, and so on.
Intercepting messages in instant messengers
Mipko Personal Monitor intercepts and records all messages in any of the instant messengers, chats and other communication applications. At the same time, both sent and received messages are recorded, which allows you to see a full dialogue.
Recording a Skype conversation
Keylogger records and transmits to you both text correspondence in Skype and recordings of voice and video chats.
Internet activity monitoring
Do you want to know exactly what sites your child is visiting? Keylogger collects relevant data for you, recording every page you visit.
Screenshots and webcam shots
Mipko Personal Monitor can be configured so that the program takes screenshots of the screen at certain intervals, and also takes pictures with a webcam so that you know exactly what is happening on the computer.
Mipko is a different program. She helped me a lot in my personal life... Many secrets in my life were revealed to me thanks to the mipko program. I don't regret purchasing this software product at all. Since computer technology has become part of people's daily lives, this software product is indispensable in the family. With the mipko software product, you always know what is happening on your PC when you are not at home... mipko has extensive capabilities, the main one of which is viewing information remotely from another PC.
Evgeniy Biryukov
Feature #1: Stealth
One of the main features of Mipko Personal Monitor is absolute invisibility during operation. The program works like invisible. And even an experienced user will not detect it.
In this case, the keylogger records any user actions on the computer. For example, communication on icq. You receive the relevant reports by email. In this case, reports are sent directly, bypassing our or any other intermediate servers.
Additionally, all information is stored on the computer's hard drive. True, it is “buried” very deeply and only you know the exact path to the folder you need. Moreover, all reports are stored in encrypted form and can only be viewed through Mipko Personal Monitor.
How much hard drive space do these reports take up? As much as you think is necessary. You set the appropriate limit in the program settings and the limit is exhausted, the keylogger simply erases old reports, recording new ones instead.
I didn’t have any interesting stories related to the program, but it helps me find passwords that were entered long ago in the history, and I recently restored access to the resource (I forgot my login). A very useful program, excellent development, you don’t see this very often, and you also have excellent technical support!
Edward Tarshikov
Feature No. 2: simple and intuitive interface

Another feature of Mipko Personal Monitor is its extremely simple interface. After all, we created this program specifically for home users.
We understand that you don't have to be computer savvy. You may have a superficial attitude about such programs. Therefore, our program does not have unnecessary functions that are not needed at home. There is no complex multi-step setup that takes an hour or two even for an experienced system administrator.
Therefore, keylogger Mipko Personal Monitor has an extremely simple interface. It, like the iPhone, is so simple and understandable that absolutely anyone can understand it - from a schoolchild to your grandmother. At the same time, the interface of Mipko Personal Monitor is 100% Russian-language, as is technical support.
I use your program to monitor my child. The child learned to erase history in the browser and was very surprised that everything remained. At the moment, the reviews are only positive.
Priuchin S.L.
Feature No. 3: friendship with antiviruses

Keylogger Mipko Personal Monitor is an observer program. It does not store any personal data of users. Doesn't steal them. She only monitors what is happening on the computer and reports it to the owner.
Moreover, only an administrator who has the appropriate password can install this software. This is an additional argument that makes keylogger an absolutely legally installed program.
Therefore, it is not legally a spyware or other application that qualifies as malicious. So Personal Monitor works well with antiviruses and goes unnoticed in 95% of cases.
What to do in the remaining 5% of cases? If you encounter Personal Monitor being blocked by your antivirus or have problems with installation, just call or write to us. And we will send you detailed step-by-step instructions for resolving this situation.
A long time ago, when I was still working as an administrator, I used your cracked program to track the work of company employees. I really liked the simple use and interface :) A few years later, I bought a single-user program to... spy on my girlfriend! She got caught cheating, and in the end this program made me a happy bachelor;)
Andrey P.
Do you already have these questions?
- How to deal with the safety of personal data?
Mipko Personal Monitor does not collect personal data and, moreover, does not send it to us. All information is stored on your computer and sent to you by email. In this case, all letters are sent directly, bypassing our servers.
- I'm on your own computer, can I install Mipko Personal Monitor?
Keylogger or what is a keylogger.
A keylogger is a small piece of equipment or program whose purpose is one thing: to intercept the characters typed from the keyboard by the victim. One of the most unpleasant programs for the user, which is used by hackers to fake the digital identity of a bona fide user.
Based on the use of special equipment, a keylogger (like the one on the left - in the section of the keyboard wire) is rarely used and requires professional skills in installation and maintenance. On the contrary, it is not so difficult to detect, and therefore we will talk about it some other time. And now I’ll tell you about interceptors in the form of software that can “work” in your system for a long time, and you won’t even know about it. We’ll talk about how to determine whether a keylogger is running on a computer at the end of the article. Let's get down to what's on the internet today on this topic. As expected, there is a lot of this goodness on the Internet. There are free programs, and there are paid versions.
What is a keylogger for?
The specifics of the program leave no shadow of doubt on the use of such utilities: it allows you to spy on the user by transmitting characters typed on the keyboard. Another question: by whom and against whom?
- It is quite understandable that parents care about their children traveling on the Internet, whose online activities begin to bother the father and mother, who, however, do not want to openly come into conflict with the child, prohibiting everything and everyone. More than once, such utilities simply help out, signaling the appearance of a child on a social network with a friend who is “a little” older and is about to realize his sick fantasies.
- It is quite a legitimate desire of the employer when he wants to make sure that the employee spends his time at the computer usefully. And, if it is not so, present the claim with evidence. At the same time, make sure that a couple of secrets did not “go to the side.”
- finally, illegal connection to the user’s computer with the aim of stealing typed passwords, logins, etc.
Keylogger Free keylogger.
Can intercept characters from the keyboard, data contained in the clipboard and network addresses from the browser address bar. There are a couple of inconspicuous functions, for example, a hidden operating mode (Ctrl+Shift+Alt+U), removing program shortcuts and hiding from the list of installed and uninstalled programs. Disadvantage of the program: in its free version, the most important function - hiding from the user's eyes - cannot be enabled. Autorun in Windows is possible, but the running program will blink treacherously from the tray. You can’t hide it from view - a window pops up notifying you that the function is available in the paid version. As are some others.

The only program window where:
- Allows the program to start immediately when the system starts
- Hide the program in the menu Start
- It will also allow you to intercept addresses in the browser and (to the right) the names of running programs
- We will notify you daily at the postal address specified in the field.
During installation, you will have to fight with the antivirus for several minutes, because neither configuration nor running the utility will escape it.
Keylogger DanuSoft
Simple and free. Also presented as a window with 4 tabs. Can hide by entering a secret word. The default is HIDEKEY, and you can force SHOWKEY to appear.

In the Log File Settings tab, you can specify the size of the document with intercepted records and, in fact, show the document itself. There are only 2 settings in the Startup Settings tab: launch with Windows and stealth mode.
Keylogger
Another simple program. After installation, you will be greeted by a colorful window. The functionality is poor, it doesn’t hide itself. But it's free. Immediately after installation, it will ask you to set a password so that the information, after interception, becomes available only to the installer:

Window of the program itself:

Keylogger REFOG Free Keylogger
The free version of the program, the manufacturer of which is quite experienced in such programs, is capable of intercepting characters typed, sites visited, and programs launched. However, I’ll warn you right away – quite a number of users have had difficulties uninstalling the program, especially the paid version, so try it at your own peril and risk. From this link you can download the latest version of the program.
Keylogger Revealer Keylogger Free
One of the most popular programs on the network. Lots of functions, easy to use. It is password protected, does not hang in the system tray, and is not visible in the settings for installing and removing programs. You should install it carefully, as some other program is asked to be installed on your computer. Screenshots will only be available in the paid version. When closed, it will warn you that it will continue to work in the background (you can return it using Ctrl+Alt+F9). The program is Russified, so you can quickly figure out the settings:

Keylogger KidLogger
Free, open source. It already knows how to work with USB devices. Records audio from a microphone and works with Skype. Log files can be viewed locally and remotely using a specially created online account. It works in hidden mode, but can be seen from the Task Manager. You can protect it with a password, but you will have to launch it from a shortcut, which in principle is not a problem, by registering the launch in Windows startup. You can download it from the link and select the desired operating system there (I have the Windows version in the archive):

Keylogger Actual Keylogger
Unlike previous programs, it is completely invisible. It cannot be seen in the Manager either; the folder with the program will be hidden, the shortcuts will not be displayed. You also cannot remove it using a traditional uninstaller. A very tricky thing. Also has password protection. Antiviruses don't like it very much. I have it in my archives. But the program is paid, install it and check out the features.

